- Electronic Signature
- Questions & Answers
- Electronic vs. digital signatures: everything you need to know
- Electronic vs. digital signatures: everything you need to know
- How to tell the difference between an electronic and digital signature
- Digital signatures: the showdown
- What are the key concepts to digital signature?
- How to create a digital signature
- How do digital signatures work?
- Why are digital signatures important?
- What certificate classes exist for digital signature?
- Which industries are the most in need of digital signatures?
- Electronic signature explained
- What makes an electronic signature legally valid?
- How can an audit trail prove your document’s authenticity?
- How to increase the security of your electronic signature
- What laws regulate electronic signatures around the world?
- How to create an electronic signature
- How to collect electronic signatures from other users
- Closing thoughts
Electronic vs. digital signatures: everything you need to know
In the past decade, electronic documentation has seen immense growth across most business segments. Every second, in every corner of the world, thousands of documents are created, processed, transferred, and, of course, signed.
More and more people choose to complete and sign documents online, which dramatically accelerates small and large-scale business processes and improves satisfaction levels. These days, being environmentally friendly while keeping documents secured and within reach doesn’t seem like such a problem. Thanks to modern-day technology, things like adding a signature to a digital document have become a one-click procedure. What’s more, with the right set of tools, the process of signing and collecting signatures can be fully automated.
When speaking about certifying digital documents, there’s still a lot of confusion around, especially regarding specific terms. It’s especially true for the terms “electronic signature” and “digital signature.” These two terms are often used interchangeably and, what’s most important, incorrectly.
Anyone new to the concept of signing documents online can be easily confused about what distinguishes electronic signatures from digital ones and how they differ in terms of tracking and legality.
It’s fair to say that confusing eSignatures with digital signatures is a common mistake typical for both rookies and professionals. The mistake you don’t want to make. Why? Because the reality is that their functions and features differ significantly.
To set the record straight, we’re here to reach deeper into the topic and clarify both terms and their meanings.
How to tell the difference between an electronic and digital signature
Let’s start with a technical definition.
A digital signature is a mathematical technique used to validate a message or digital document’s authenticity and integrity. On the other hand, an electronic signature is a symbol attached to a document and executed or adopted by a person with the intent to sign it.
Simply put, an electronic signature is a symbol attached to a document that is used by the individual who intends to sign it. Above all, it shows the intent to sign the document or form. When two or more people want to come to an agreement, they show their commitment by signing a document that later becomes legally binding between them.
Suppose you have a delivery, and a courier asks you to sign using their iPad. In that case, the image you’ll draw is, in fact, your electronic signature. Capturing your handwritten signature with your phone’s camera and attaching it to an outgoing email is also considered an electronic signature.
In contrast, a digital signature lacks this visual component. Instead, it’s a mathematical scheme used to:
- Prove the authenticity of a document and its source.
- Ensure that the document has not been tampered with.
- Verify the signer’s identity.
Unlike electronic signatures, digital signatures are mainly used to authenticate a user’s access or specific action. A digital signature’s primary purpose is to secure a document so that it’s not tampered with, except for the authorized user(s). In everyday life, we deal with digital signatures when conducting payments and banking operations.
To better understand the differences between electronic and digital signatures, see the side-by-side comparison below:
Digital signature
- Uses a certificate-based ID to demonstrate proof of signing and authenticate a signer’s identity.
- Uses encryption to link the signature to a signed document and prove its validity.
- A bit hard to understand and implement.
- Used to secure document integrity.
- Isn’t the same as a handwritten signature.
Electronic signature
- Uses an array of methods, e.g., email or phone verification, to demonstrate proof of signing and authenticate the signer’s identity.
- Uses audit trail methods to link the signature to a signed document and prove its validity
- Easy to implement into existing workflows.
- Used to verify document authenticity.
- Is a digitized version of a handwritten signature.
To sum up, the preferred type of signature is determined by multiple factors, such as the type of document you want to sign as well as the level of authenticity expected. More details about the difference between digital and electronic signatures are provided below.
Digital signatures: the showdown
As mentioned above, a digital signature is a mathematical algorithm used to validate the authenticity and integrity of a message, transaction, or, most commonly, digital document. The validation is achieved by generating a unique hash of the message or document and encrypting it using the sender's private key.
Another cool thing about digital signatures is that they make it difficult for the signer to deny having signed something. The digital signature is unique to both the signer and the document and binds them together.
Therefore, digital signatures can provide the added assurances of evidence of origin and status of an electronic document and acknowledge informed consent by the signer. They also increase the transparency of online interactions and develop trust between vendors and customers or business partners.
What are the key concepts to digital signature?
Although the concept of establishing a secure communication using cryptography dates back to ancient times, digital signatures became a reality in the 1970s — thanks to the development of Public-Key Cryptography (PKC).
In order to learn how digital signatures work, we need first to understand the main principles of hash functions and PKC:
- Hash functions. Hashing is one of the milestones of a digital signature ecosystem. The process of hashing involves transforming data of any size into a fixed-size output. Usually, it is achieved with the help of algorithms known as hash functions.
A hash function, or simply a "hash," is a fixed-length string of numbers and letters generated using a mathematical algorithm. It is a one-way function unique to the hashed document, which means you can put data into a hashing algorithm and get a unique string. Still, if you come upon a new hash, you cannot decipher the input data it represents. A unique piece of data will always produce the same hash.
- The output generated by a hash function is called a hash value. When combined with cryptography, hash functions can be used to create a hash value that acts as a unique digital fingerprint. It means that any change in the input data would result in a completely different hash value. That's the number one reason why hash functions are so widely used for verifying the authenticity of digital data.
- Public key cryptography, or asymmetric encryption, is an encryption technique that uses a pair of strings known as keys. The private key encrypts the data and is kept secret. The public key, on the other hand, decrypts the data and is distributed openly to recipients. Public key cryptography can be used to ensure the confidentiality, integrity, and authenticity of a digital document or message.
- Public key infrastructure (PKI) consists of policies, standards, people, and systems that support the distribution of public keys. It also provides the identity validation of individuals or entities with digital certificates and a certificate authority.
- Certificate authority (CA) is a trusted third party that validates the document owner's identity. It generates a key pair on their behalf or associates an existing key provided by the person to that person. Once a CA verifies someone's identity, they issue a digital certificate that can be used to verify an individual associated with a public key when requested.
- Digital certificate. A digital certificate is an electronic document that binds together a public key with an owner's identity. It verifies that a particular public key belongs to a specific person. In a way, digital certificates are similar to driver licenses. Their purpose is to identify the holder of a certificate. Digital certificates contain the public key associated with the document or message as well as other information about the organization, individual, and the certificate authority.
- Pretty Good Privacy (PGP) is an alternative to PKI, also known as the "Web of trust." It is a relatively informal mechanism for determining the validity of public keys. Anyone who trusts the signer to follow proper identification procedures can decide to trust all the keys signed by that person.
This system contrasts with traditional public-key methods because there are no central signing authorities. Once the signer verifies the person's identity with the new key (for example, by meeting them in person or by voice recognition on the phone), the signer verifies that the new key is genuine.
The security of a digital signature almost entirely depends on how well the private key is protected. Using digital signatures together with PKI or PGP strengthens them and reduces the possibility of a security breach.
Without PGP or PKI, validating someone's identity or revoking a corrupted key is impossible. It could cause things like fraudulent impersonation when an imposter steals another person’s digital identity.
How to create a digital signature
Let's take a brief look at the steps required to generate a digital signature for a particular document or message:
- Step 1. A hash value is generated using the selected hashing algorithm.
- Step 2. A unique key pair is generated.
- Step 3. The hash value generated earlier gets encrypted.
- Step 4. A digital certificate associated with the key pair is created. It’s then used for communication between the sender and recipient.
The encrypted hash — along with other information, such as the hashing algorithm — is, in fact, the digital signature you're looking for.
How do digital signatures work?
Digital signatures work by verifying that a digital message or document was not modified — intentionally or unintentionally — since the moment it was signed. To achieve this, a unique hash of the message or document is generated and encrypted using the sender's private key.
Once completed, the message or document is digitally signed and sent to the recipient. The recipient generates their own hash and decrypts the sender's hash (included in the original message) using the sender's public key. The recipient then compares the hash they've generated against the sender's decrypted hash. If the two hashes match, it means that the message or digital document has not been modified and the sender is authenticated.
The creation of a digital signature system typically comprises the three following steps:
- Hashing. The first step is to hash the message or document. This is done by applying a hashing algorithm so that a hash value is generated. Hashes always have the same length, regardless of how much data you feed into it. For example, the MD5 formula always produces a 32 character-long hash.
- Signing. After the data is hashed, the message or document's sender needs to sign it with a private key. The recipient checks its validity by using the corresponding public key provided by the signer. If the private key is not included, the recipient won't be able to use the corresponding public key to verify its validity. The sender of the message generates both public and private keys, but only the public key is shared with the receiver.
- Verifying. Imagine that the sender writes a message to the recipient, hashes it, and combines the hash value with the private key to generate a digital signature. The recipient verifies the digital signature by using the sender's public key. It reverses the signing process and produces a hash value upon which the digital signature was created. The hash values are then compared. If they match, it means that the digital signature could only have been produced by the person with access to the sender's private signing key. If the two hash values do not match, then such a signature is considered invalid. If anyone attempts to change the document, the two hashes will not match and this fact will be easily detected.
In other words, digital signature technology requires all the parties involved to trust that the signature creator managed to keep their private key secret. If someone else has access to the signer's private key, that party could create fraudulent digital signatures on behalf of the private key holder.
Why are digital signatures important?
Digital signatures are mainly used to achieve three results: data integrity, authentication, and non-repudiation.
- Data integrity. The recipient can verify that the document has or hasn't been changed. Any modification would produce a completely different digital signature.
- Authenticity. As long as the sender's private key is kept secret, the recipient can use the public key to prove that the sender and no one else created the particular digital signature.
- Non-repudiation. Once the signature has been generated, the sender won't be able to deny having signed it in the future, unless his or her private key gets somehow compromised.
What certificate classes exist for digital signature?
There are mainly three classes of digital signature certificates, each used for different purposes.
- Class 1. Class 1 certificates are usually issued to individuals and private subscribers. These certificates confirm that the user's name and email address comes from a specific subject within the certifying authorities database. Class 1 certificates cannot be used for legal business documents. They are validated based only on an email ID and username. They only provide a basic security level and are used in environments with a low risk of data compromise.
- Class 2. These certificates can be issued to both business and private users. Class 2 certificates confirm that the subscriber's information does not conflict with the information in well-recognized consumer databases. Class 2 certificates are mainly used for e-filing of tax documents,e.g., Income Tax Returns and Goods and Services Tax Returns. They authenticate a signer's identity by reconciling it with data from a pre-verified database. These certificates are used in environments where the risks and consequences of data compromise are moderate.
- Class 3. The highest level of digital signature certificates. It’s considered a high assurance certificate, primarily intended for e-commerce applications. This certificate can be issued to both individuals and organizations only on their personal appearance before the Certifying Authorities. In simple words, it requires a person or organization to present in front of a certificate authority to prove their identity before signing. Class 3 digital signature certificates are used for e-auctions, e-tendering, e-ticketing, court filings, and other environments where potential data threats or the consequences of a security failure are high.
Which industries are the most in need of digital signatures?
The digital signature market’s growth is driven by the growing demand to eliminate fraud, encourage technological innovations, improve data integrity, scalability, and transparency.
A digital signature has already become the gold standard for efficiency and security across many areas of business. The top industries that use digital signatures include:
- Financial services. Financial institutions use digital signatures for paperless banking, credit/loan form processing, mortgages, insurance documentation, and more. Also, since 2018, it's possible to legally notarize documents online. Since it's a heavily regulated sector, digital signatures should be used in compliance with the regulations imposed by the Electronic Signatures in Global and National Commerce Act (ESIGN Act) and state UETA regulations.
- Government. Digital signatures are adopted by government institutions for a variety of uses, including processing tax returns, verifying business-to-government transactions, ratifying laws, and managing contracts. The U.S. Government Publishing Office, for example, publishes electronic versions of budgets, public and private laws and congressional bills with digital signatures.
- Manufacturing. Manufacturing companies use digital signatures to streamline processes related to product design, quality assurance, manufacturing enhancements, marketing and sales. Digital signatures in manufacturing are governed by the International Organization for Standardization (ISO) and the National Institute of Standards and Technology (NIST).
- Healthcare. Healthcare institutions use digital signatures to improve the efficiency of treatment and administrative processes (such as e-prescribing and hospital admissions) and strengthen data security. Thanks to digital signatures, healthcare workers can maintain full client security and confidentiality — a crucial security measure for any modern business. The use of digital signatures in healthcare must comply with the 1996 Health Insurance Portability and Accountability Act (HIPAA).
Most modern-day software supports digital signatures and digital certificates, making it easy to validate the authenticity and data integrity of communications and transactions conducted online.
Electronic signature explained
One of the most significant advantages of electronic signatures, when compared to digital ones, is their relative simplicity. There's no need to code or encrypt anything. You can quickly sign any documents online in one click by uploading an image of your autograph from your device, writing it with your device’s trackpad or touchscreen, and so on. In addition to that, electronic signatures allow businesses and individuals to process paper-driven workflows exponentially faster, eliminating the need for printing, scanning, mailing, and hard-copy filing.
Following the arrival of the COVID-19 pandemic, social distancing measures, and the mass shift to working from home, electronic signatures began rising in popularity. Businesses still needed to conduct their operations, but they quickly realized that an eSignature solution is probably the only way to stay afloat in the absence of office equipment.
While being much simpler to set up, electronic signatures are often considered less secure than digital signatures. But is that actually true?
The answer is: it all depends on what eSignature service you’re using at the moment and whether its security measures match your business needs. In other words, the signing method you choose should, above all, fit the occasion in terms of security and usability.
Along with eSigning, it's important to have your data protected from malware threats, hacking attacks, and identity theft. If the software you're using is equipped with extra security measures (such as advanced threat protection, multi-factor authentication, downloadable document history, and comprehensive audit trails), you can be rest assured that each of your documents is reliably eSigned and securely stored. In that regard, an electronic signature can be considered just as secure as a digital signature.
What makes an electronic signature legally valid?
An electronic signature is a process that indicates the acceptance of a document or record. It's a single-factor authorization that verifies a signer's identity with proof of signing achieved via an audit trail embedded within each digital page.
To be considered valid, the eSigning process should meet the following requirements:
- Both parties consent to using an electronic signature.
- The process of eSignature creation is recorded.
- Records of electronic signatures are retained and made available for accurate reproduction.
An electronically signed document may be legally valid but ruled inadmissible in court due to the lack of audit logs or authentication weaknesses. That’s why it’s critical that you choose an eSignature solution that is highly reputable and meets the following technical requirements:
-
- Unique signatures for each user. When a document is sent for signature, the signer creates a unique signature that is attributable to him/her, and no one else.
- Signer authentication. Information used to identify signers includes an email address they used when signing the document, IP address, and exact time of document access. The option to add two-factor authentication to any document sent for signature should also be available.
- Cloud retention. Documents are housed in secure cloud storage facilities. Any registered user who signed or took action in connection with a particular document should be able to view or download a copy of the final eSigned document.
- Detailed audit log. An audit log shows the entire history of a document, including uploading, adding elements, viewing, signing, and who took each of these actions. The audit log should be viewable directly from the eSignature app you’re using.
- Security. Compliance with industry-leading security standards, such as HIPAA for medical documentation, will give you and your business one of the most secure eSigning experiences available.
How can an audit trail prove your document’s authenticity?
An audit trail allows you to track every event in your electronic document’s history. It serves as fully court-admissible evidence that proves who accessed a particular document, who made changes in it, who signed it and when exactly all of that took place.
Excuses like "We never got an email from you" or "You probably sent the document to the wrong guy who signed it by mistake" will never work here.
The key factor here as to why the audit trail data is treated as court-admissible is because it is fully compliant with all UETA regulations regarding attribution.
With an audit trail, your document activity and electronic signatures will always be protected, valid, and accepted.
In addition to audit trails, modern-day electronic signature solutions, such as airSlate SignNow, provide users with an option to track document changes via the Document History function.
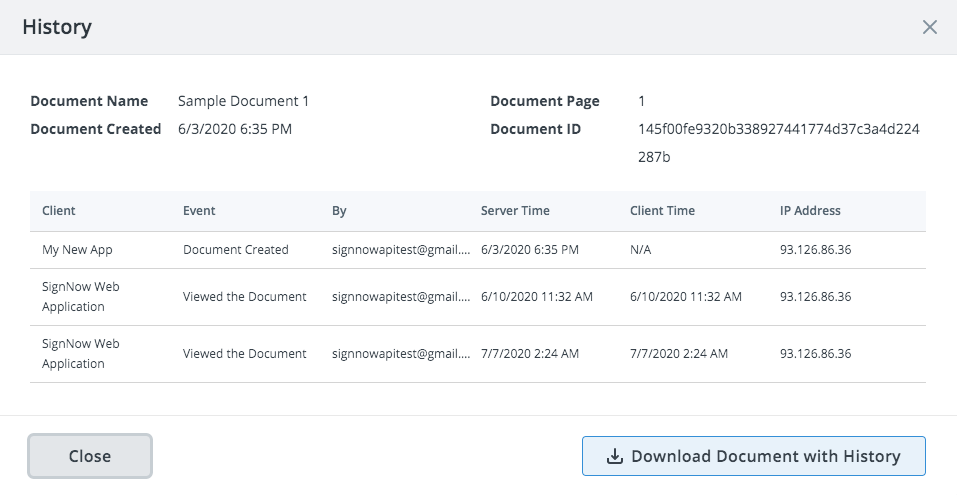
Document History is a log that contains all actions that have been taken in the document, alongside timestamps, IP addresses and other parameters.
How to increase the security of your electronic signature
While authenticated digital signatures provide cryptographic proof that the stated entity signed a document and that the document has not been altered since then, not all electronic signatures can provide the same guarantees.
Below are the most commonly used security measures you can apply to increase your electronic signature's security and protect your document from unauthorized access:
- Dual factor authentication. Dual factor authentication is a user verification technique that requires a signer to enter their credentials one more time before accessing the document. This ensures that the signer is, in fact, the intended recipient of your document.
- Authentication timeout. The authentication timeout can be enabled so that your signer must re-login for every set period of time. This will ensure a better level of security for your document and the sensitive data it may hold.
- Phone call authentication. You can protect your document by requiring authentication with a phone call. Once your document has been signed, you will receive an instant notification.
- Document password. Ensure that your recipient is the only person capable of viewing, editing, and signing your document by adding a password.
- Identity verification. Require your signer to use Touch ID on their mobile device or verify a signer's identity using a photo.
- Advanced threat protection. Advanced threat protection is an enterprise-level feature that offers protection against complex malware or hacking attacks that target sensitive data within an organization.
What laws regulate electronic signatures around the world?
From all the variety of countries that have enacted electronic signature legislation, only a few have adopted laws and policies that stand out for their thoroughness and inclusivity. Some of the most important regulations regarding electronic signatures around the world are listed below:
- United States: The Electronic Signatures in Global and National Commerce Act. The ESIGN Act ensures the validity of electronic signature records only if they accurately reflect the agreement and can be reproduced as required. When choosing an electronic signature solution, make sure it allows you to download copies of any signed document.
- Canada: The Personal Information Protection and Electronic Documents Act states that electronic signatures are just as valid as traditional handwritten signatures. However, as of now, wills, power of attorney contracts, and real estate contracts cannot be signed electronically.
- European Union: The Electronic Identification and Authentication and Trust Services (eIDAS) regulation states that an electronic signature is only valid if all parties involved in the signing process consent to use it.
- China: Originally the Electronic Signature Law of the People's Republic of China, and later the amended eSignature Law, states that electronic signatures are legal for civil contracts. However, they aren't recognized for real estate deals, public-utilities suspensions, inheritance documentation, adoption papers or marriage licenses.
How to create an electronic signature
Let's see what a basic eSignature workflow looks like within an enterprise-level electronic signature app, such as airSlate SignNow.
Step 1. To get started, choose a document that you want to eSign. You can either pick an existing document or template from your airSlate SignNow Documents folder or import a new document from your device's storage. airSlate SignNow supports all the popular document formats, including DOCX, PPTX, JPG, PNG, and PDF.
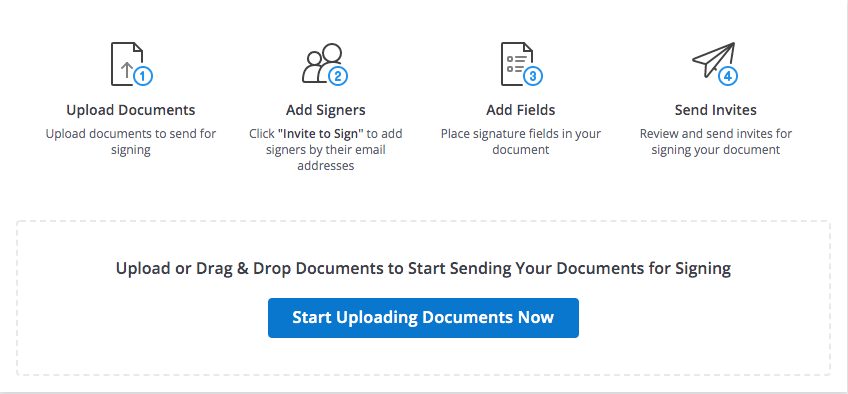
Step 2. Use the PDF editor to customize your document according to your needs before eSigning it or sending it out for signature. If your document needs to be signed by other signers except yourself, use the Tools section of the airSlate SignNow editor. Here, you can add necessary fillable fields and assign them to your signer(s). You can add/remove signers and set a signing order by clicking the Edit Signers button.
If you like to edit the document and then eSign it yourself, use the Edit & Sign section of the airSlate SignNow editor. It allows you to place permanent text or signatures on a document.
Click/tap the respective field to activate it. Once you've activated the field, click the body of the document to indicate where you want your signers to put the requested information. You can also drag and drop fields directly onto the document.

Step 3. Click the Signature Field to start signing. A new window will pop up, where you can specify how you want to eSign your PDF. The following options are available:
- Upload an image of your handwritten signature from your device in JPG, GIF, or PNG formats. The image you upload must be less than 4 Mb.
- Draw your signature using your mouse or trackpad.
- Type in your full name and choose one of the automatically generated samples. Click the Change style button to select a style for your signature.
- Additionally, the airSlate SignNow mobile app enables you to import files from your Photo Library, capture documents using your smartphone's camera, and even collect in-person signatures with your iPad or tablet in Kiosk Mode.
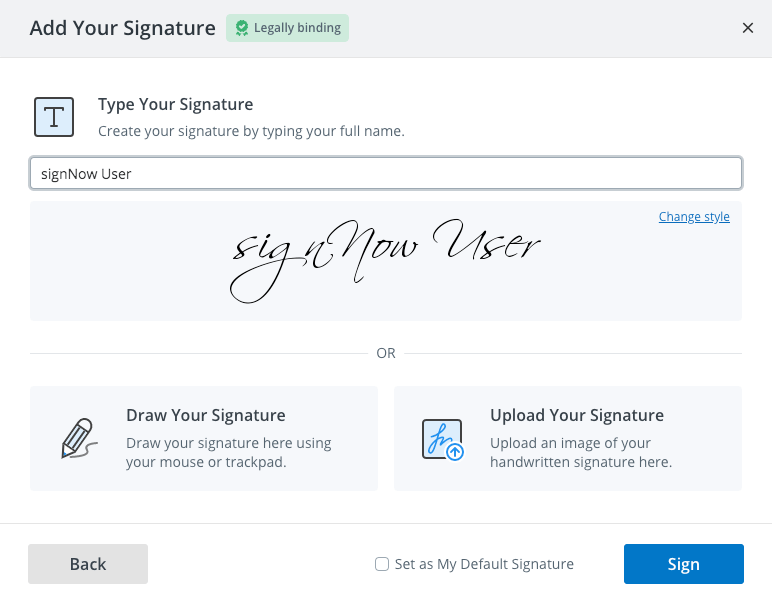
Step 4. Check the Set as My Default Signature bar to save your signature for later use. If everything looks OK, click Sign. Remember, you cannot remove or edit your signature once you've signed a document. By saving changes made to a document, you confirm that it cannot be altered in any way.
That's it. Your PDF has been successfully signed! Click Save and Close to return to the Documents folder.
There are many other ways you can modfy your PDFs in airSlate SignNow. For example, you can download the document to your device, download a document’s History, archive it, rename it, move it to another folder, and much more.
Keep in mind that you cannot edit documents once they’re completed. If you view a signed document, you'll notice there's no option to edit or update it. Once you've signed a document, you can't go back and edit your eSignature, add fields, convert it to a template, or generate a new signing link.
How to collect electronic signatures from other users
Send a signature invite
The easiest and the quickest way to send a document for signing in airSlate SignNow is by clicking the Invite to Sign button. In the new window, fill in the signer's email (if there is more than one signer, add each signer's email) and carbon copy anyone else who needs to track the signing process. If necessary, personalize the signing invitation for your recipient by creating a customized message. Specify a signing order if you wish to invite more than one person to eSign your form or contract.
Click Advanced Option for additional settings. Set an expiration date or add reminders for the document that you send out for signature. Extend the expiration date from a minimum of 30 days to a maximum time frame of 180 days. You can also set an automatic reminder email to be sent or provide the recipient with the option of forwarding the invite email to someone else.
Request signer authentication to ensure your document cannot be accessed by anyone other than your intended recipient. Add a second layer of authentication by setting a password for your document or have a password automatically generated and sent to your recipient as a text message. Once all the parameters are set, simply click Send invite.
Create a signing link
airSlate SignNow allows you to collect signatures via signing links. A signing link is a unique link to a document that you can distribute to others. Each person who visits the signing link can sign their own fresh copy of the document.
Click the Create Signing Link button next to the document and copy the link. You can copy your signing link and paste it into emails, post it on websites, blog posts, etc.
A signing link won't expire unless you make edits to or delete a document, or if a guest signer enters the signing session. As a document owner, you can track the signer's IP address and other information related to the signing process. To do so, simply click the Download with History button.
Send a freeform signature invite
A freeform invite gives the sender the option to send a document to a signer without fields. When the signer receives the document, he or she inserts fields manually, anywhere they want. Freeform invites can be beneficial and time-efficient for the sender, however always double-check that the signer fully signed and completed all the essential requirements for your document.
Signers can drag and drop fields (Signature, Text, Date/Time, or Checkboxes) onto the document, adjust the field locations, and remove the fields, if needed. Using the freeform invite makes the document sending process simpler and more comfortable for the sender, too.
Your signer will receive an email containing the invitation to sign the document. Once they open it, the signer will be prompted to input their name. Then they can start inserting fields.
Closing thoughts
Today, as never before, businesses and individuals realize that digital transformation is not so much about advanced technology, outstanding experience or innovative advantages. It's about moving your business forward and opening doors to new opportunities.
Customers no longer want to waste their time and tend to choose the easiest way to get their documents processed. The more simple things are, the more significant and noticeable they are to customers.
The coronavirus-caused prevalence of at-home work has further reinforced the importance of paperless, eSigning workflows. The understanding of fundamental paperless document management and its concepts will help your business speed up its operations, reduce paper waste, start collaborating digitally and protect your data and documents.
Find everything you need to know about the ins and outs of managing your document electronically in our Questions & Answers section. Here you can find all the necessary tips and step-by-step instructions for managing and eSigning your documents.

- Electronic vs. digital signatures: everything you need to know
- How to tell the difference between an electronic and digital signature
- Digital signatures: the showdown
- What are the key concepts to digital signature?
- How to create a digital signature
- How do digital signatures work?
- Why are digital signatures important?
- What certificate classes exist for digital signature?
- Which industries are the most in need of digital signatures?
- Electronic signature explained
- What makes an electronic signature legally valid?
- How can an audit trail prove your document’s authenticity?
- How to increase the security of your electronic signature
- What laws regulate electronic signatures around the world?
- How to create an electronic signature
- How to collect electronic signatures from other users
- Closing thoughts
Related questions
Business Cloud
Automate business processes with the ultimate suite of tools that are customizable for any use case.
-
Award-winning eSignature. Approve, deliver, and eSign documents to conduct business anywhere and anytime.
-
End-to-end online PDF editor. Create, edit, and manage PDF documents and forms in the cloud.
-
Online library of 85K+ state-specific legal forms. Find up-to-date legal forms and form packages for any use case in one place.